
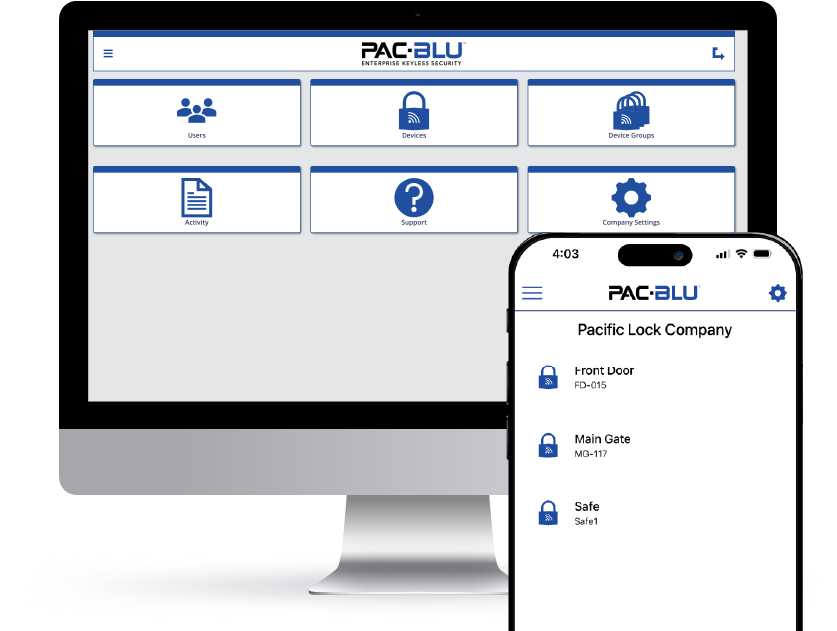
PAC-BLU redefines industry standards by lowering up-front system costs and simplifying installation. With simplicity and security in mind, PAC-BLU is the easiest way to setup Cloud-Based Access Control for your company or organization.
Choosing PAC-BLU means investing in a future where access control is seamless, security is uncompromisable, and business operations are more efficient. It’s an ideal solution for any organization looking to modernize their access control and embrace the digital transformation of security.
- Mobile Credentials
- Cloud-Based Management
- No Ethernet Required
- Detailed Audit Trails
- Unlimited Users & eKeys
- Customizable Access Levels
- Instant Access Revocation
- Time-Based eKeys
- Offline Access Mode
- AES-128 Bit Encyption
- Biometric Authentication
- Scalable System Design
How It Works
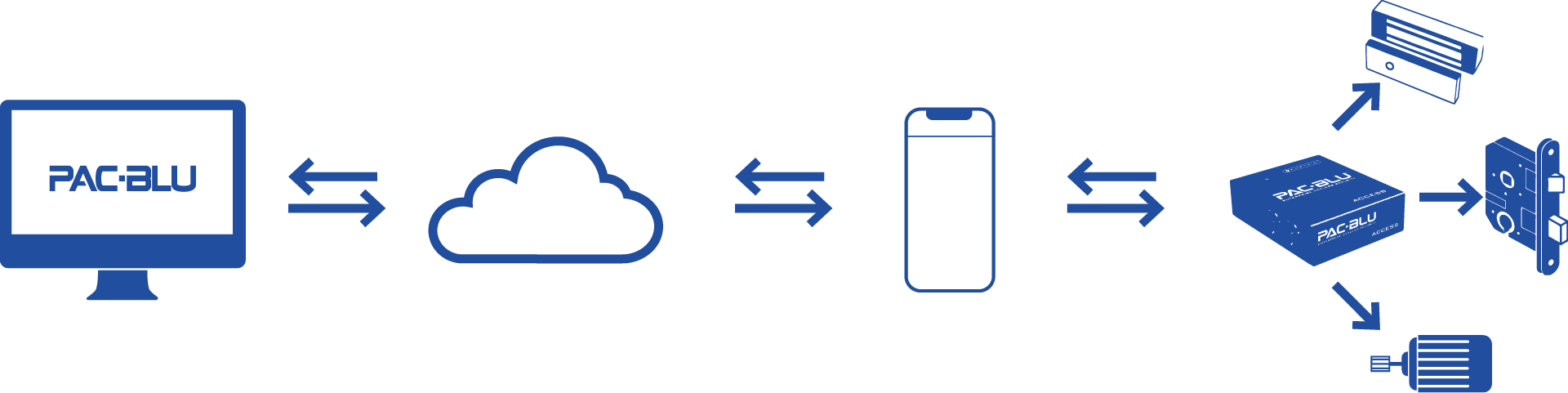
Web App
Your portal for managing user permissions, assigning eKeys and viewing audit trails for all devices throughout your company.
Cloud
PAC-BLU’s cloud-based technology secures your data with TLS asymmetric cryptography and AES-128 bit encryption standards.
Mobile App
Your phone becomes your key. Bluetooth Low Energy allows for energy savings and extended-range communication.
Controller
The Access controls electric strikes, drop bolts, DC motors, electromagnets, cabinet locks, and other endpoints.
Traditional
Access Control Problems
User-UNfriendly
Traditional systems are outdated, cumbersome and non-intuitive, making daily management and usage a hassle for administrators and users alike.
Complex Installs. Rising Costs.
Copied, Lost, and Stolen Keys
is the solution

Simple. Easy. Powerful.
PAC-BLU transforms your smartphone into powerful mobile credentials, removing the reliance on traditional card readers, cards, and fobs. Additionally, no PoE requirements means less installation time and associated costs, while still providing powerful, cloud-based management features in the Sentinel web app.

Low Cost. High Tech.
PAC-BLU is the easiest solution to transition from a traditional key system into a keyless access control system – complete with audit trails, eKey management, and a myriad of features only possible with electronic access control. PAC-BLU’s “hub-less” design offers lower installation costs, while providing increased versatility and scalability.
Secure Mobile Credentials
Far more secure and convenient, mobile credentials are the antidote to traditional access methods, putting an end to key duplication and RFID “sniffing” attacks. Advanced encryption and authentication protocols ensure your data is protected while keeping user management simple and easy.
Applications & Industries
Education & Institutional
Offices & Administration
Healthcare Environments
- Lower administration costs and decrease credential deployment time
- View detailed audit trails throughout your organization
- Assign date and time-based eKeys
- Simple installation process significantly reduces costs
- Secure access to schedule II drugs
- Quickly assign or remove credentials
Commercial & Manufacturing
Off-the-Grid Installations
Transportation Industry
- Lower administration costs and credential deployment time
- No CAT5 or Ethernet cable runs
- Continuous operation without an internet connection
- Significantly reduced installation costs versus a traditional system
- View detailed audit trails on all assets
- Continuous operation without an internet connection
Mobile Access Control
PAC-BLU redefines industry standards by lowering up-front system costs and simplifying installation. With simplicity and security in mind, PAC-BLU is the easiest way to setup Cloud-Based Access Control for your company or organization.
Roll-Up Doors
Available Q3'24

- Offline Access Mode
- Extended Battery Life
- Easy eKey Management
- Quick & Easy Installation
- Detailed Audit Trails
- AES-128 Bit Encryption
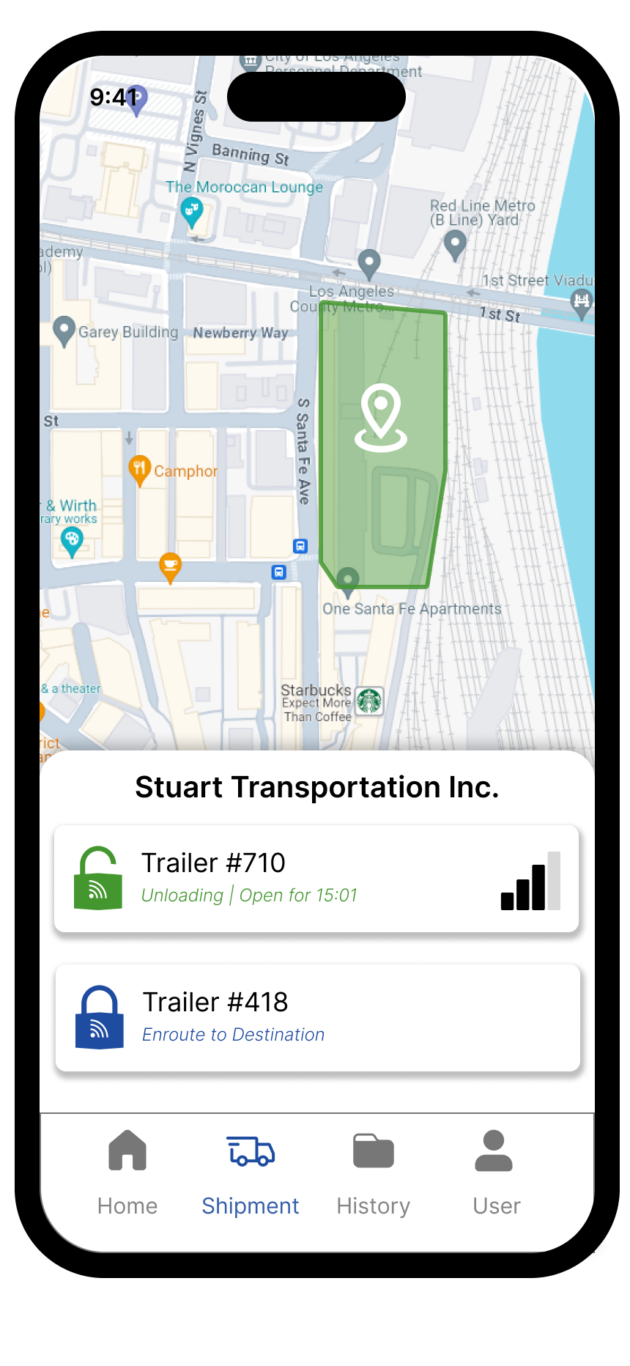
Location-Based eKeys

PB-Access
Intelligent Bluetooth Opening Controller
Simplified Installation
No hub required – the Access communicates directly with the users smartphone via Bluetooth. No need for lengthy cable runs.
Powerful Versatility
Control a variety of endpoints, ensure uninterrupted access with dual power inputs, easily wire a REX, and monitor door status with multiple sensors.
Enterprise-Ready
Expand your system with as many Access controllers as needed. No extra costs for extra users, add as many as needed.
No Reader Required
Don’t hassle with extra installation time. Simply mount the Access and assign eKeys to your user’s smartphones.
Backup Power Inputs
Multi-Sensor Support
Advanced Endpoint Control
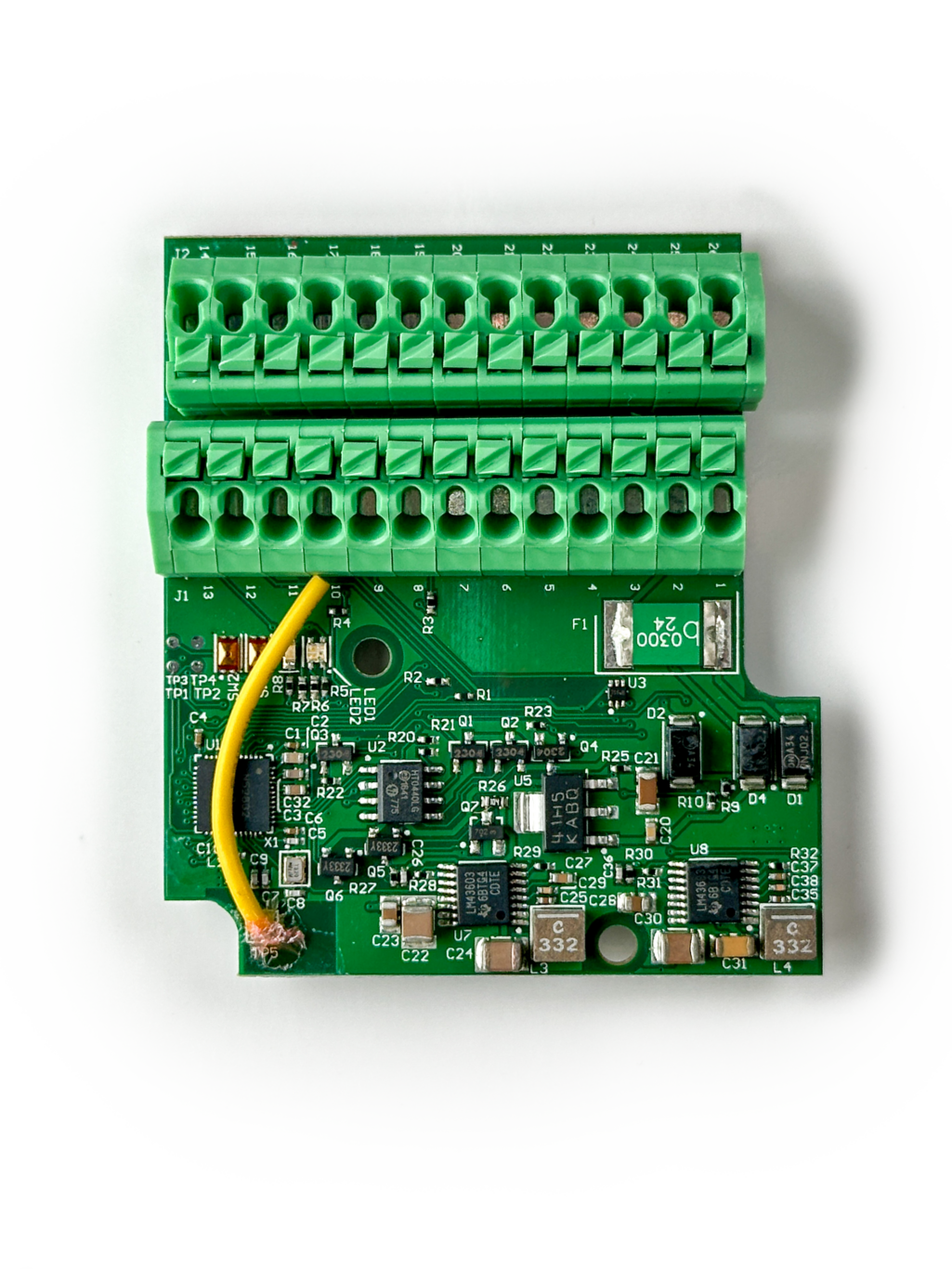
Push-In Connectors
Mobile Credentials
REX Support
Specifications
General
- Single Door/Device Controller
- BLE v5 2.4 GHz Communication
- Assigned Users: Unlimited
- Assigned eKeys: Unlimited
- Dimensions: 2.8 in x 3.4 in x 1.1 in
- Weight: 0.52 lbs
In The Box
- Access Controller
- Wiring Diagram
- Scan-able QR Support Docs
Connectivity/Power
- 6 to 24 VDC Input Power
- 3A Maximum Output
Security
- AES 128-bit Encryption
- PKI Technology with Cryptographic Key
- Exchange Protocol
- Unique BLE Session Tokens
- Two-Factor Authentication
- Web-Based Session Tokens
- Intrusion Detection

The PAC-BLU System
Sentinel
Web-Based, Cloud Management
Add, Remove, and Manage Users
Full-Access, Time-Based, or One-Time eKeys
View Audit Trails and Activity Logs
NexGen
Mobile Smartphone App
Installers can setup and modify PB-Access devices
End Users use eKeys as mobile credentials

Sentinel
eKey Management
Access Control. Anywhere.
At the heart of PAC-BLU is the “Sentinel” web management platform. Unlike traditional access control solutions, PAC-BLU’s Sentinel offers easy management of thousands of PAC-BLU devices and end-points – saving installers and administrators time and money.
Unlike many other systems out there, PAC-BLU has no limit on the number of users or devices connected into an enterprise system. Sentinel also centralizes management and assignment of users, eKeys, and time schedules. The system is easy to use and has a clean user experience.
Cloud-Based Security
With advanced capabilities to easily modify access schedules, grant access, and revoke access for a group of users, the web portal elegantly bypasses the need to scroll through lists of users to make quick changes. “Sentinel” also powerfully links access with accountability. It enables proactive monitoring of your locks’ access history, ensuring users are held in compliance with your enterprise policies for authorized access.
Powerful Management Tools
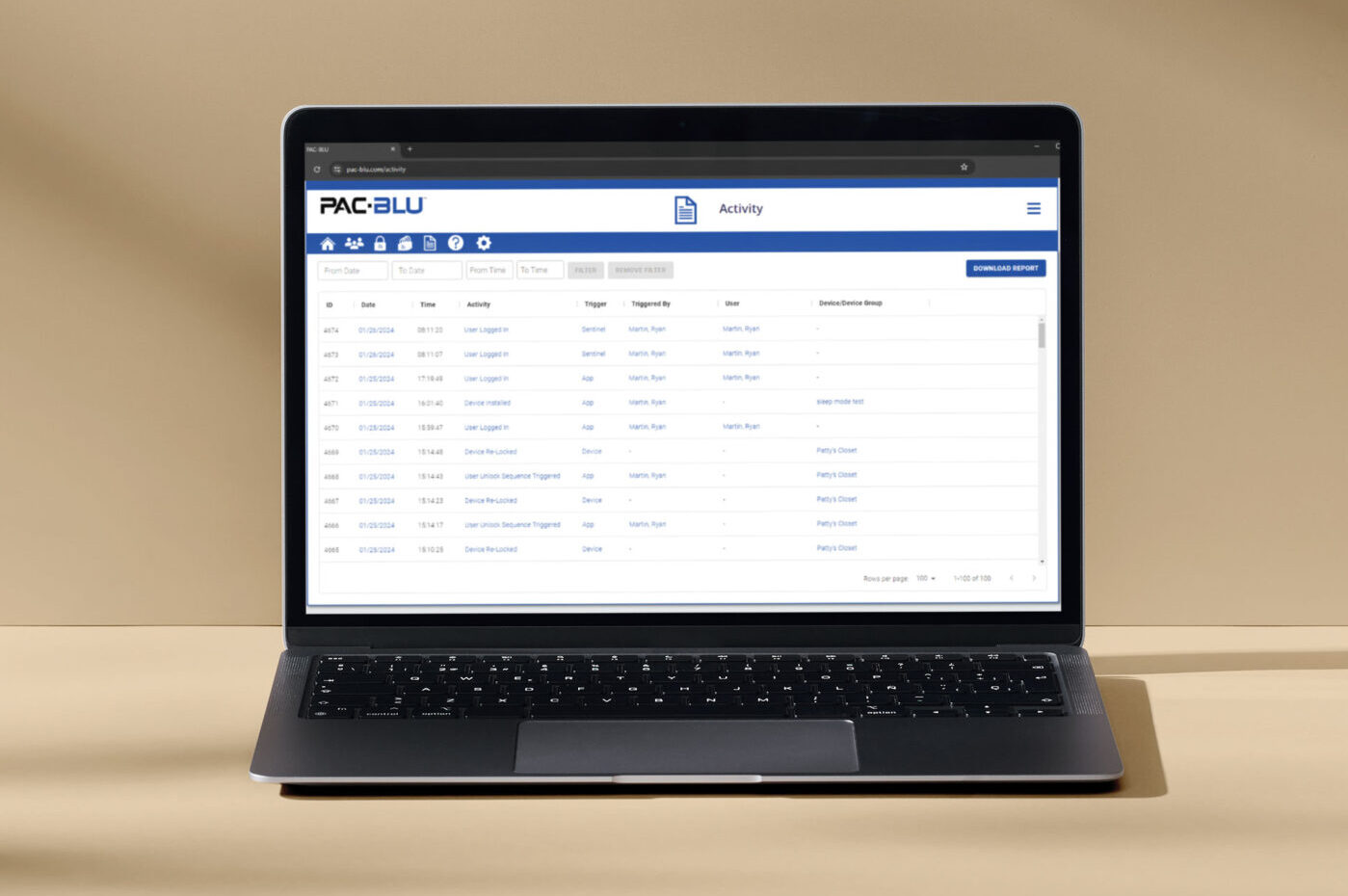
Detailed Audit Trails
View a comprehensive record of all access events, with detailed monitoring and analysis of security data in real time.
Device Groups
Organize devices to streamline management and save time on deploying credentials for users.
Access Levels
Define and manage access levels within Sentinel and assign full-access, time-based, user-based, or one-time eKeys.
Mobile Credentials
Never cut a key again! Turn smartphones into keys and remove the hassle of traditional access control systems.
Global Settings
Implement uniform security policies and configurations across your entire network, ensuring consistent access control and system behavior.
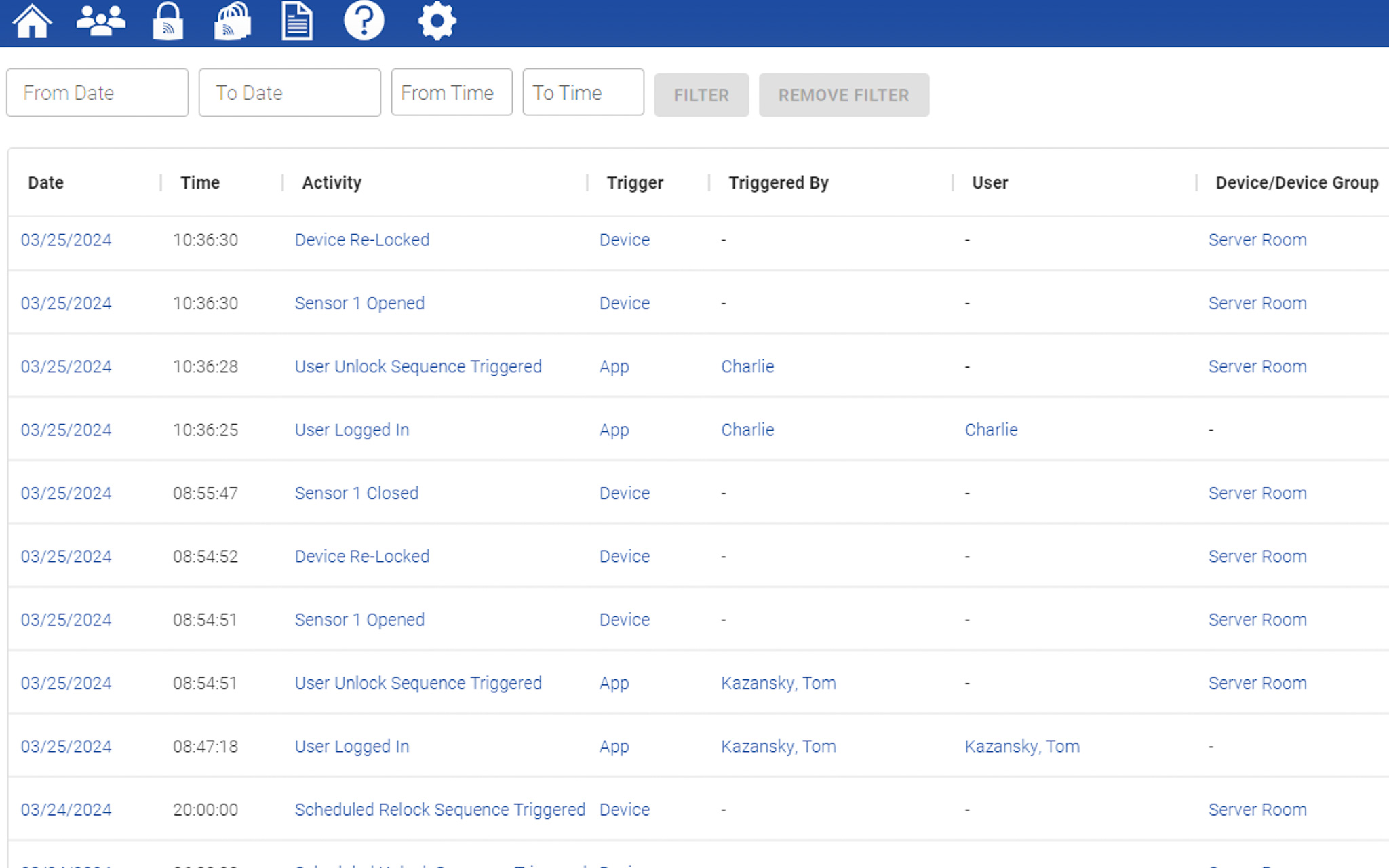
Audit Trails
Get Accurate Data
In traditional access control environments, keys and fobs can be stolen, shared, or duplicated – leading to inaccurate audit trails.
PAC-BLU utilizes mobile credentials to provide security managers with accurate activity logs, empowering them to promptly take action on accurate data. Audit trails record a history of all types of events including unlocks, relocks, eKey assignments, and device modifications.
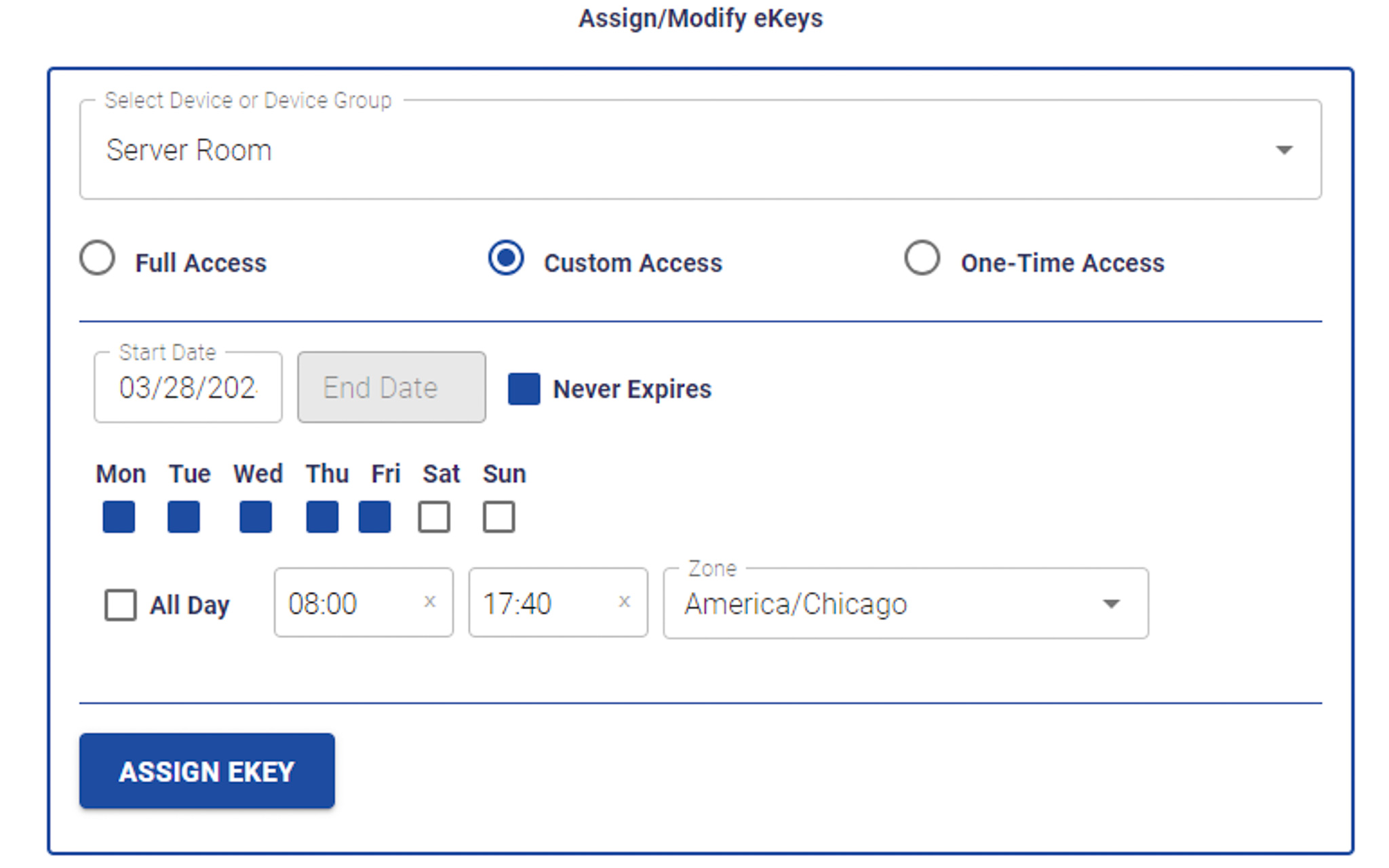
Assign eKeys
eKey Flexibility
In PAC-BLU, administrators wield unparalleled control through customizable eKey capabilities. Whether granting full access privileges, establishing time-based restrictions, enabling one-time-use keys, or setting expiration and start dates, administrators tailor access permissions to match specific needs.
This granular control ensures optimal security and flexibility, empowering administrators to adapt access permissions seamlessly to evolving requirements.
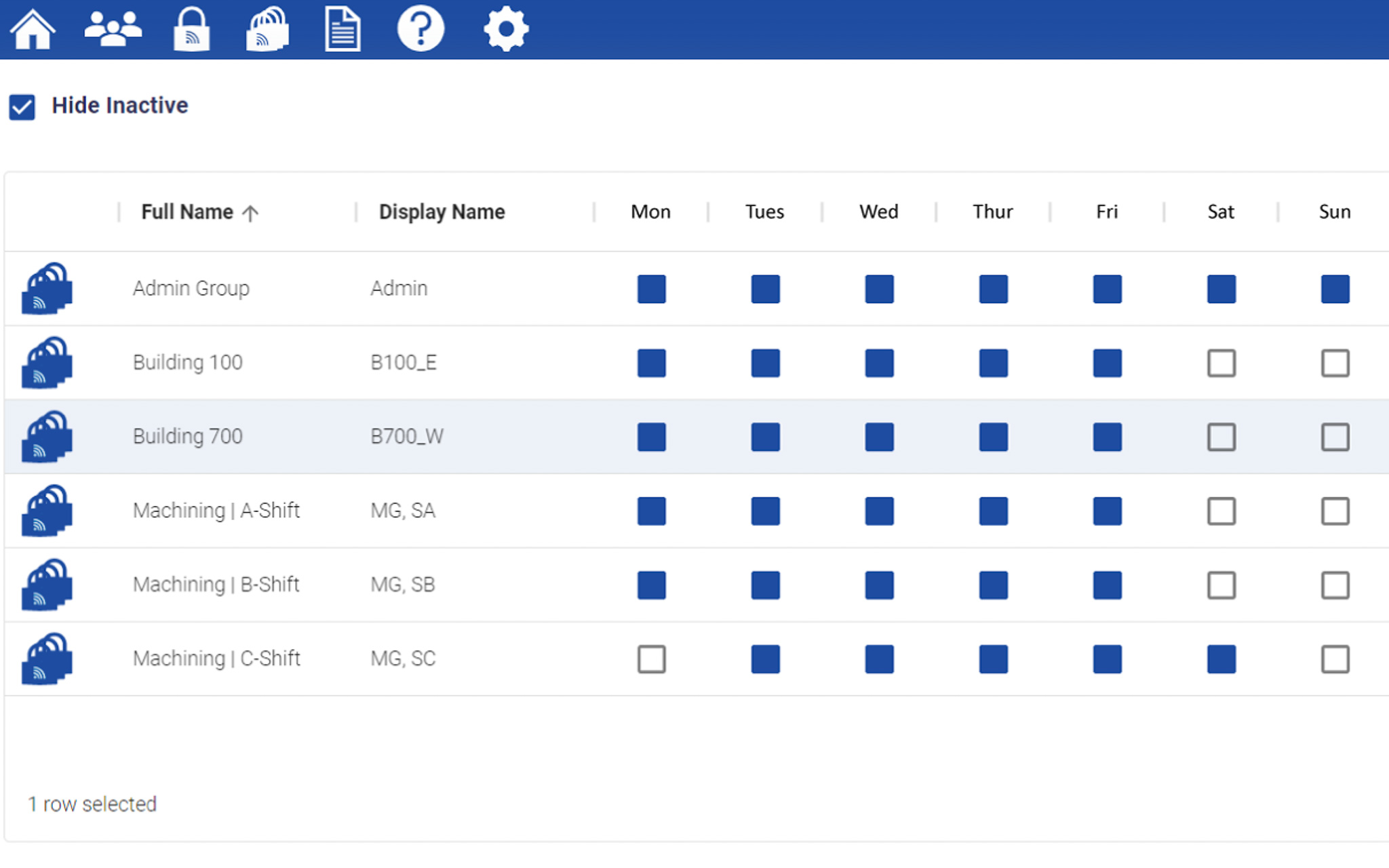
Device Groups
Save Time Assigning eKeys
Device Groups save time by simplifying eKey distribution for system administrators. For instance, administrators can create groups based on working shifts, ensuring that employees have access to the required areas during their designated hours. Alternatively, groups can be organized by building, allowing seamless access management tailored to different locations within a facility.
This flexibility empowers administrators to optimize access control strategies according to specific operational needs, enhancing efficiency and security across diverse environments.
NexGen Mobile App
Simplified Credential Process
Save time and money by remotely distributing credentials through Sentinel’s Web Management portal and securely store eKeys directly on an individual’s phone.
Instant and Easy Access
NexGen provides users with quick and seamless access to secure areas. Mobile credentials are assigned in real time to immediately provide or remove access from individuals.
In-App Configuration
Users assigned “Installer” permissions in Sentinel have the ability to change lock types, set dwell time, auto-relock timers, and more customizations directly in the app.
Enhanced Security Posture
Utilizing AES-128 bit encryption, unique session tokens, PKI technology, and cryptographic key exchange, NexGen provides end-to-end security for all users.
Support Sustainability
Transitioning to digital credentials with NexGen significantly reduces the environmental impact associated with traditional physical access systems.

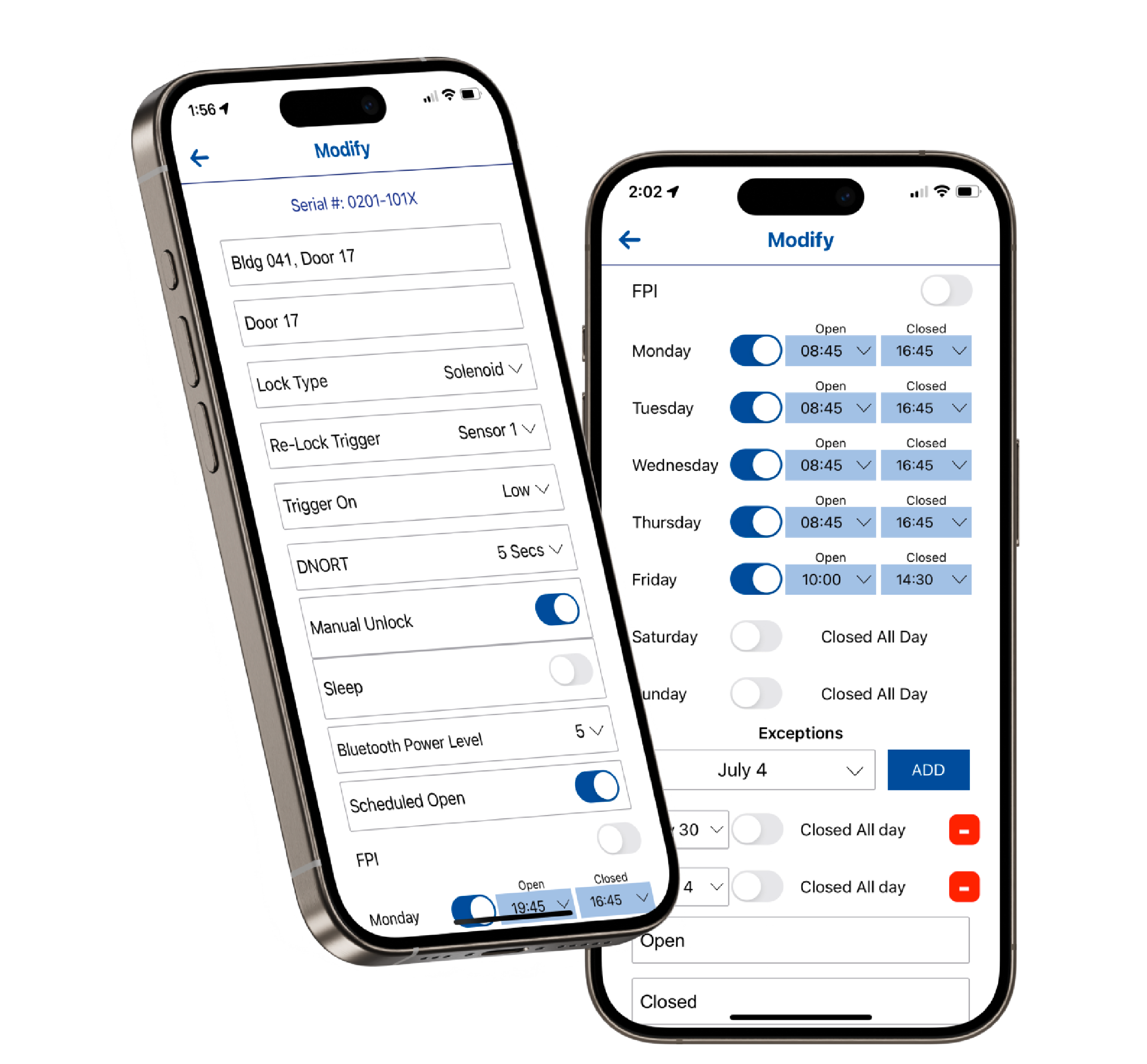
Complete Control.
From Your Phone.
Purposefully designed to be the simplest electronic device you own, PAC-BLU simplifies the way you setup and make changes to your locks by giving you access directly from your phone.
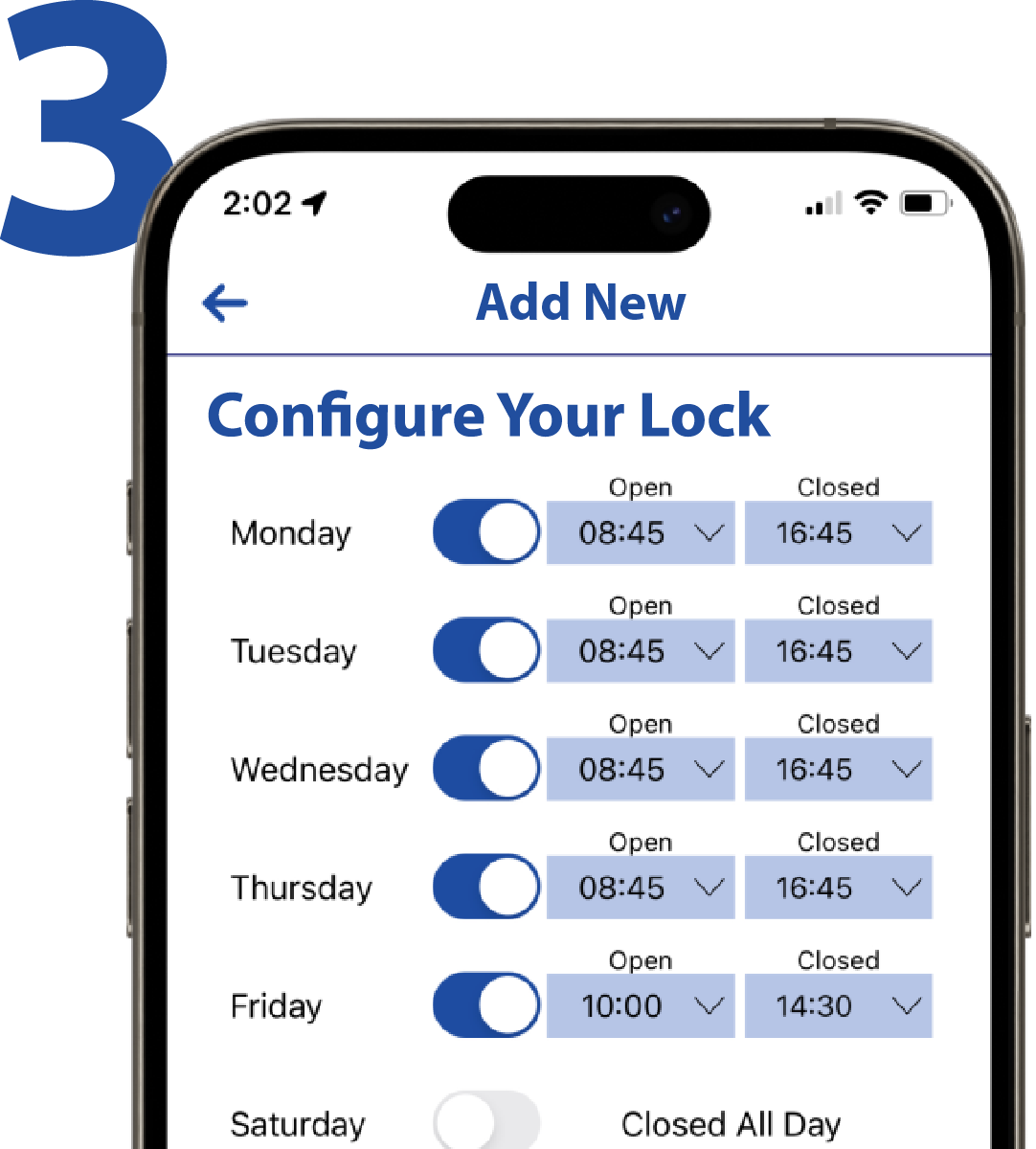
Once a user is assigned “Installer” permissions in Sentinel, they have the ability to add, modify, and remove locks from your organization. Lock names, lock types, scheduled opens, re-lock triggers, sensor configuration, and schedule exceptions can all be managed from the NexGen app.

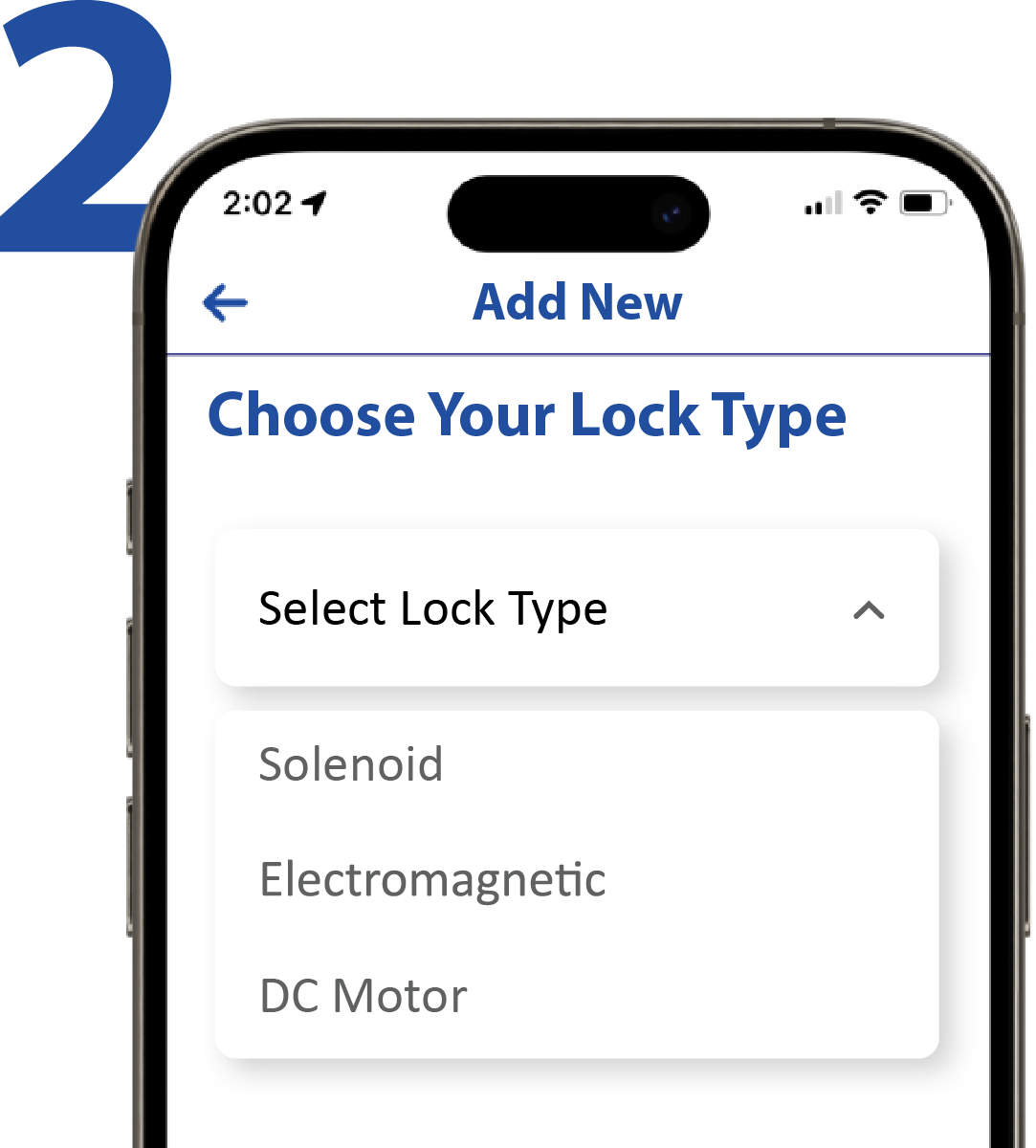
- Lock Type Selection
- Request-to-Exit Setup
- Configurable Auto-Locking
- Create Holiday Exceptions
- Manage Scheduled Opens
- Control Unlock Distance
Easy Device Setup
Installing and configuring a PAC-BLU device is quick and easy. After connecting your lock to both power and your locking endpoint, open the mobile app to view the device you’d like to add to your company. Simply “tap” the lock to add it to your company and follow the simple instructions to turn your smartphone into a key for any door with a PAC-BLU device! Adding a request-to-exit button or door sensor is as easy as wiring it in and enabling it in the app.
TFB2
Tri-Function Unit
Backup Power Input, LED, & Wake Button Support
Ensure uninterrupted system operation during power outages with the TFB2, a versatile accessory for the Access Series. Simply connect a 9V battery to the terminal for continued power until power is restored.
Moreover, the TFB2’s wake button can be used to activate your Access from its low-power sleep mode, extending battery life in battery-operated systems. The TFB2 also ensures users can easily monitor the lock’s status with a multi-color LED, providing added assurance and peace of mind.
9V Battery Terminal
LED Indicator
Reset/Wake Button

Increased Reliability
IP65 Weatherproof
Off-Grid Solutions

Specifications
General
- IP65 Rated All-Weather Cover
- 4-Color LED Indicator
- Easy-Connect 9V Terminals
- TFB2 Dimensions: 1.3” x 1.3” x 1.3”
- Mounting Kit Dimensions: 2.5” x 2.5” x 1.7”
In The Box
- TFB2
- Installation Instructions
Surface Mount Kit (Optional)
- Surface Mount
- Mounting Hardware
Frequently Asked Questions
What is PAC-BLU?
PAC-BLU is a simple, cloud-based access control system that turns your smartphone into a key, offering a secure way to unlock doors. It’s designed to make access management straightforward and key-free for everyone, while prioritizing security.
How does PAC-BLU work?
PAC-BLU operates through a cloud platform that communicates with installed hardware via a users mobile phone, allowing users to manage access permissions and monitor entry points from anywhere.
Do I need an internet connection for PAC-BLU?
An internet connection is required for real-time monitoring and system management, but local functionalities remain operational even off-line.
What devices are compatible with PAC-BLU?
PAC-BLU works with iOS and Android smartphones, tablets, and any web-enabled device for monitoring and management.
Do I need to install a credential reader?
No, the Access acts as both the “door controller” and the “credential reader.” Mobile credentials are granted access via Bluetooth communication.
Can I use PAC-BLU across multiple locations?
Yes, PAC-BLU’s cloud-based system allows you to manage access control for multiple locations from a single dashboard.
Is PAC-BLU secure?
Absolutely. PAC-BLU utilizes AES-128-bit encryption methods, TLS cryptographic standards, and secure data-at-rest protocols to ensure the highest level of security for your data.
What if my power goes out?
PAC-BLU devices are equipped with two independent power inputs, making it easy for you to install a battery backup or use our “TFB2” to provide emergency power with a 9V battery.
Where can I install PAC-BLU?
If a traditional key and cylinder can control access, then PAC-BLU can replace that antiquated solution with a system that grants or removes access in real time.
Can I grant temporary access with PAC-BLU?
Absolutely. PAC-BLU allows you to create temporary or time-limited access permissions for individuals in addition to creating scheduled unlocks to fit your organizations needs.
Does PAC-BLU offer audit trails?
Yes, PAC-BLU provides detailed audit trails, recording every access event to increase your organizations security posture.
How do I manage access permissions with PAC-BLU?
Access permissions can be easily managed through the PAC-BLU web portal, Sentinel, making it easy for you to add, remove, or modify user access rights from anywhere.
Do I need to run Ethernet cables throughout my building?
No, PAC-BLU tremendously simplifies access control installations by only requiring hard-line or battery power to each access point.
How many users does PAC-BLU support?
There is no limit to the number of users you can assign to each access point.
How do I update PAC-BLU software?
Web portal updates are published in real-time to keep your systems up-to-date. Firmware updates are performed Over-the-Air via your mobile device.
Who do I contact if I need support?
Each company’s system administrator is the primary support partner. In cases where more support is needed, PAC-BLU authorized installers receive support tickets and work to resolve potential issues.
Does the Access connect to the internet?
Not directly. The Access communicates to an individual’s mobile phone securely via the NexGen App and the mobile phone communicates to the internet using Wi-fi or cellular services.
How do I install PAC-BLU?
PAC-BLU offers a simple installation process. However, we recommend professional installation to ensure optimal setup and integration.
Is there a subscription fee for PAC-BLU?
Yes, as iOS, Android, and web technologies evolve, the PAC-BLU development team works to keep your data safe and secure, along with providing continuous cloud access, updates, and support.
Need A Custom Solution?
The flexibility of PAC-BLU shines in custom security solutions. At PACLOCK, we design security solutions uniquely for each application, instead of creating general designs that do an OK job across an entire industry. If you’re searching for a security solution, tailored to your company, we’d love to work with you!
Rapid Prototyping
As a US manufacturer, we can rapidly design and produce prototypes to provide you with excellent solutions.
Custom Integration
Using existing software? We can work with your current software to seamlessly integrate PAC-BLU and improve operational efficiency.
Scalable Solutions
PAC-BLU is designed with the future in mind, employing cutting-edge technologies and a robust architecture to accommodate future growth and expansion.
Cost Savings
Drive down costs associated with access control maintenance, administration, and security breaches by leveraging PAC-BLU.

